The answer is yes, but as all things in life, it’s a bit more complicated. AiProtection was added to the Asus routers about five years ago when the Taiwanese manufacturer partnered with Trend Micro to develop a suite of security-focused features as a means to add a new layer of protection to your network (and to gain an edge over its competitors, obviously). Some called it a gimmick, others praised it, but ultimately, it was a nice addition for a time when online security was finally starting being taken more seriously, but it was also a time when privacy was becoming a secondary objective. Not much has changed today, and besides some new controversy here and there (see the WhatsApp fiasco), people still prefer to not being bothered configuring some complicated system.
And that’s what AiProtection aims to do, you flip a switch and it starts working on its own, blocking potentially dangerous websites and more (you don’t have to configure anything – everything is done for you in the background). I have seen that both Netgear and TP-Link have immediately added their own set of security features (Netgear Armor by Bitdefender and TP-Link HomeCare which is also from Trend Micro) and, as you can see, the manufacturers have decided to leave the security aspect of their routers to a third party, therefore trusting the expertise gained over the years by security dedicated entities. And it may have been a very wise decision since all have a wide database of dangerous websites, as well as the means to keep intrusive players at bay. But, considering that the consumer-grade router is nowhere near powerful enough to have all (or at least some of) these features built-in, you do have to rely on the communication with the Trend Micro’s servers. So how does it exactly work?
How does AiProtection (by Trend Micro) work?
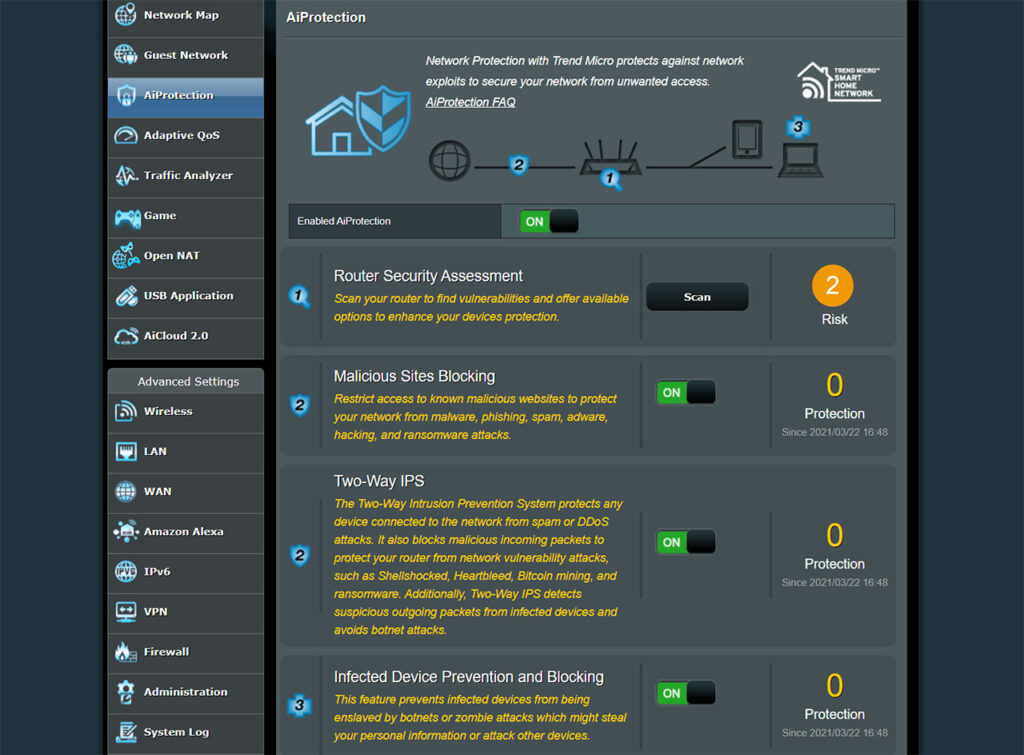
The AiProtection is divided into two sections (as seen on an Asus RT-AX82U updated to the firmware version 3.0.0.4.384_9948), there’s the Network Protection and the Parental Controls. Since the latter is a native feature that has nothing to do with Trend Micro, we’re going to focus on the Network Protection which is divided into four sections.
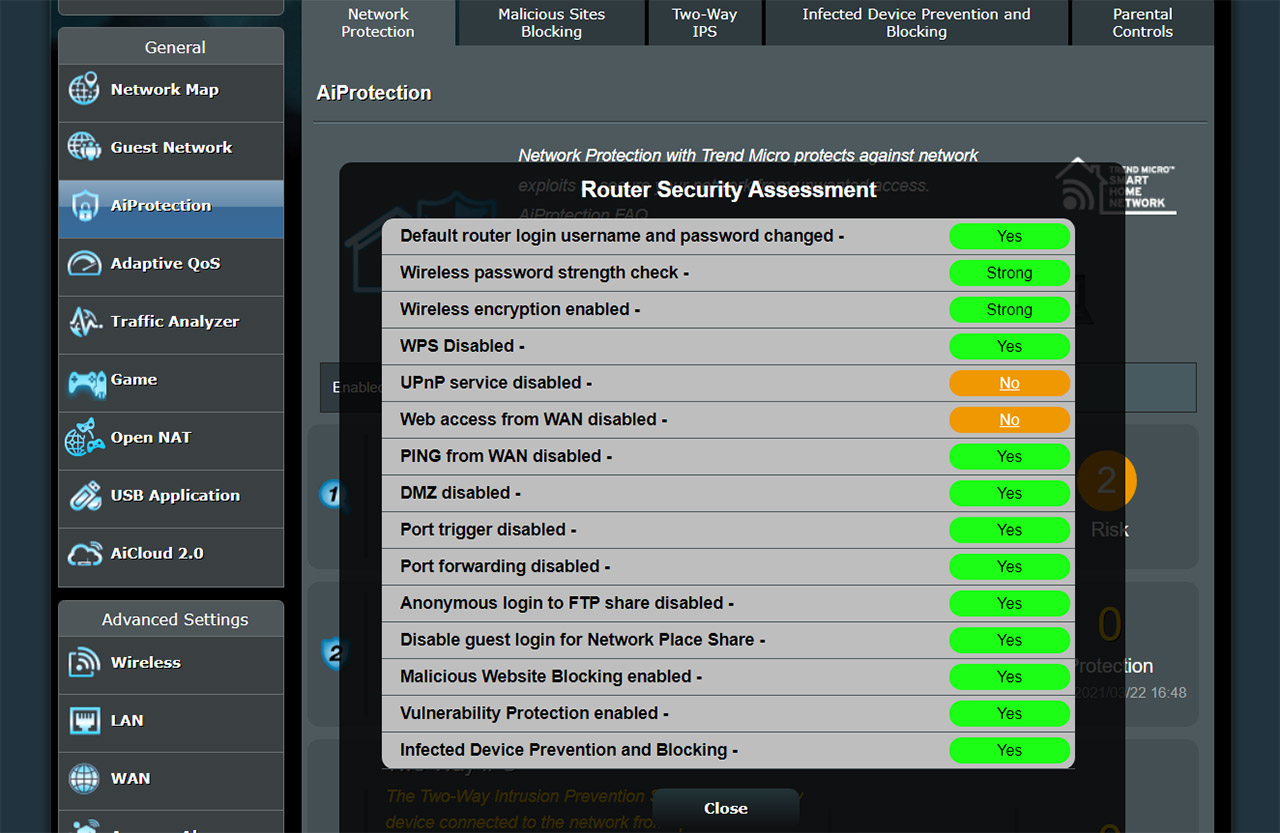
There’s the Router Security Assessment, the Malicious Site Blocking, the Two-Way IPS and the Infected Device Prevention and Blocking. After running the Router Security Assessment, you will get a list of the best practices that all people should perform to make sure their network is protected. This utility scans whether the user has or has not disabled some potentially dangerous features (such as WPS) and whether there is wireless encryption enabled, as well as if the admin username and password has been changed (the minimum security measures that anyone can take).
But, at the same time, know that some of these features need to remain enabled in order for specific applications to work (for example UPnP, Port forwarding or FTP sharing), so, following this guide blindly can lead to some issue – but hey, your router is definitely more secure!
The Malicious Sites Blocking is most likely what most people will find the most intrusive since it needs to check the websites that you’re visiting and see if it matches any record from Trend Micro’s large database – if it does, then the website is blocked, otherwise, it’s going to be considered safe. In case a new dangerous website is accessed for the first time by a user, Trend Micro will not block the access to it since it’s not yet part of the database, but, as soon as the scans detect that that website is indeed dangerous, it automatically updates the database for all Asus router users (that have available AiProtection), so no other user will have its computer, router or entire network infected.
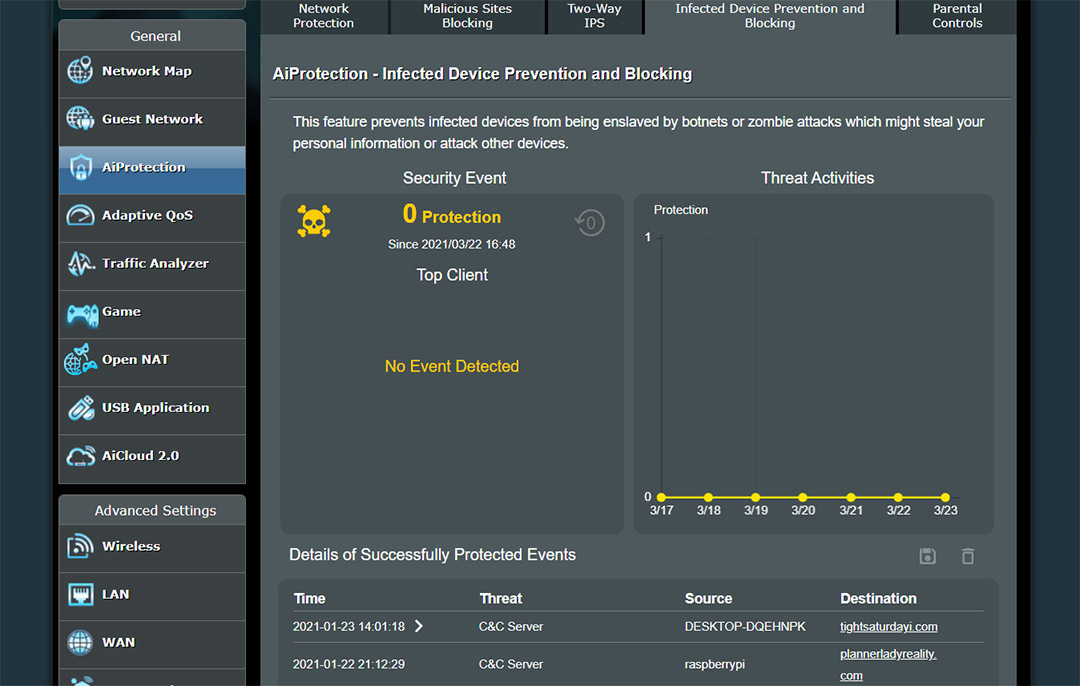
And this takes us to the Two-Way Intrusion Prevention System which is designed to prevent connected devices from receiving spam and DDoS attacks by blocking incoming malicious packets (I doubt that they check each packet individually and it’s most likely done by simply checking the source), as well as checking out any suspicious outgoing packets that can suggest that one of your devices may be infected – this usually happens with botnets. Since the IPS engine is closed-source and on Trend Micro’s servers, there have been several issues over the years, such as problems with webcams (even from Nest, not some Chinese knock-off) or with crypto-mining and you will have to wait until Trend Micro (not Asus) updates its database (if you’re in a hurry, you could temporarily disable the Two-Way IPS). Lastly, there’s the Infected Device Prevention and Blocking which again, ties in with the previous feature and it has the role of blocking attacks coming from compromised devices from your network.
It could be one of your own devices or it could be someone visiting you and their laptop is infected (without their knowledge, hopefully), and it’s trying to infect other client devices from your own network. Since all these features are so tied together, how exactly does disabling one not affecting the functionality of the other – I assume it’s because the same amount of data is sent to Trend Micro regardless of the enabled feature. And this does seem to be right considering that Trend Micro still receives some data from your router even if you disabled AiProtection (you need to withdraw from the agreement to stop the data sharing). And this gets us to the next section.
What data is being sent to the Trend Micro servers?
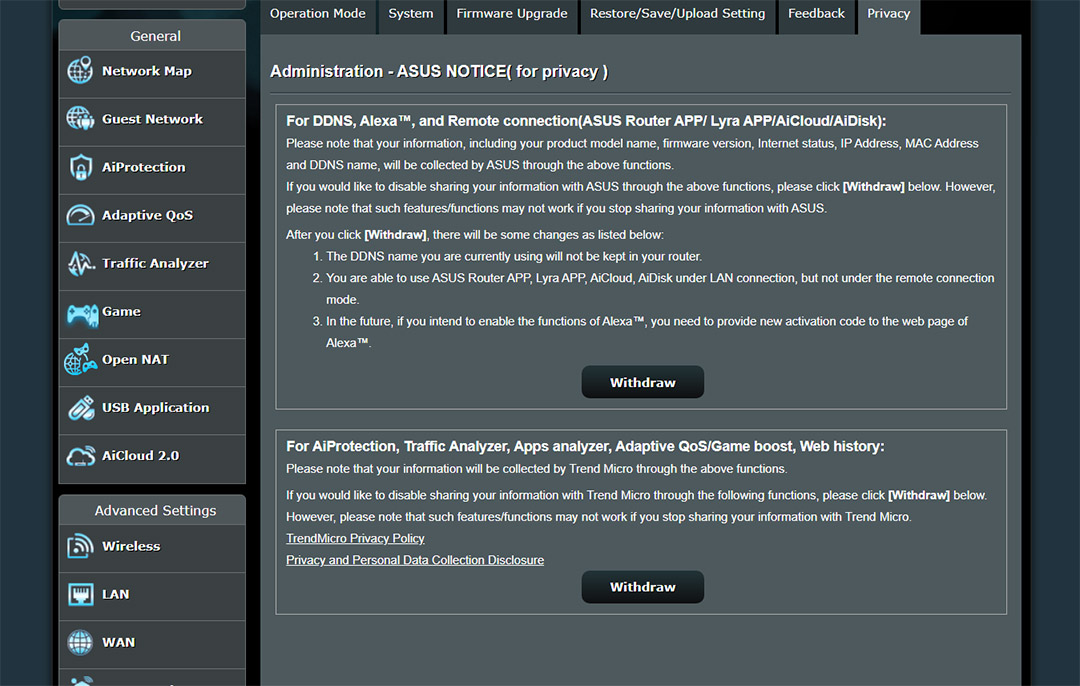
First, it’s best to simply check the Trend Micro disclosure for what data it can collect – it doesn’t mean that it does collect everything that’s mentioned, it means that it can, so legally, they can’t be held accountable in the future (it’s required by their lawyers). Obviously, we, as consumers, should never take the side of large corporations since all businesses care is about making a profit (in a legal manner, for maintaining the tone of the discussion). If you log into the Asus router web-based GUI and then go to Administration > Privacy and select TrendMicro Privacy Policy and the Privacy and Personal Data Collection Disclosure, you can find out yourself what data is collected and how it’s being processed (or if it’s being shared with third-parties).
To make matters as simple as possible, this is some of the info that I was able to find (as taken directly from the Privacy notice), but be aware that it’s still quite broad and does cover more applications (or products) – it still offers some insight about what can be seen by Trend Micro:
• Product information, such as MAC address, device ID
• Public IP address of the user’s gateway to the internet
• Mobile/PC environment
• Metadata from suspicious executable files
• URLs, Domains and IP addresses of websites visited (which answers the question in the title of this article)
• Metadata of user/device managed by gateway Product
• Application behaviours
• Personal information contained within email content or files to which Trend Micro is provided access
• Behaviours of Product users
• Information from suspicious email, including sender and receiver email address, and attachments
• Detected malicious file information
• Detected malicious network connection information
• Debug logs
• Network Architecture/Topology
• Screen capture of errors
Yes, there’s quite a bit of info that can be collected by Trend Micro and you need to agree to it, so their services can work, which are described in detail here:
• Analyse data sent to/from the user’s device to isolate and identify threats, vulnerabilities, suspicious activity and attacks;
• Assess the reputation of a website, email sender’s IP address, device or file to advise the user on whether access should be granted;
• Analyse email to protect against spam, impersonation and other suspicious content;
• Virus protection;
• Intrusion detection, prevention and protection;
• Threat prevention and prediction;
• Network defence;
• Sand box testing (for certain cloud products);
• Storage of emails for back up purposes (certain cloud products);
• Identify, block and/or remove applications, messages, and files that may compromise productivity or the performance and security of computers, systems, and/or networks;
• Identify sources and methods of targeted attacks; and
• Deliver updated protection against malicious threats.
The collected information can also be used for other purposes such as:
• Internal record keeping;
• Compliance with the law and requests from government bodies;
• Product and Service development;
• Keeping existing and past Customers informed about our Products, Services and promotions;
• Providing Customer support;
• Managing subscriptions and billing; and
• Responding to requests, questions and comments.
This is the legal document which is better read by a lawyer to fully grasp some nuances (that may be lost to people outside the legal specialty, such as myself), but Trend Micro does provide a simplified version here, which does say that the IP address, the URL, the Source and Destination IP address, the file and file path, as well as the GUID will be collected. This is necessary in order to ensure that their services can detect any malicious URLs (and C&C servers), to identify the devices that are connected to your home network, to scan the packets and so on.
Lastly, it’s worth taking a look at with whom is Trend Micro sharing your data. From the Privacy notice, it seems that some data can be shared but only in relation to provide or receive certain services which can include technical support, hosting cloud services, shipping and customer research. The last is a bit ambiguous but overall, it doesn’t seem that Trend Micro will sell your data to ad companies, that’s something that other bigger players are well known to practice and yes, I am talking about Google, Facebook and other social media websites (funny enough, Microsoft and Apple can also be included in this list).
Since I have several Asus routers, I hooked up one of them to the Internet (an RT-AX82U) and connected a couple of client devices. Afterwards, I ran Wireshark to see if I can capture some movements to and from Trend Micro’s servers. And I did see some data going and coming from them (trendmicro.com.edgekey.net and docs.trendmicro.com – there was also some CDN traffic from Akamai, although I am not entirely sure if it’s related to Trend Micro or not), but what surprised me was the amount of communication with Google servers, Amazon servers and, from time to time, the communication with Microsoft (although I did try my best to keep them out of my computer).
Obviously, this isn’t a case “they do it too, so it’s fine”, but to show how much data is being collected from us without our knowledge, but with full consent (most of the time given without thinking about it).
Can we trust Trend Micro with our data?
There have been two instances when Trend Micro ‘got in trouble’, the first time, with some apps that were collecting browser history data from Apple devices (as seen on the 9to5mac.com) and the second time it was an ex employee that went rogue and impersonated Trend Micro representatives to steal and sell customer data (check the article on ZDnet.com).
Furthermore, just like most (if not all) other similar companies, it was only after GDPR, that Trend Micro has added a lot more transparency into the data collecting practices, which started the discussions in 2018 (as expected) of whether we shouldn’t be more careful about sharing our data. At the same time, Trend Micro has been in the online security business for over three decades and it has been ensuring the online security of both small and large companies; it also partnered with lots of networking manufacturers, such as Cisco, Barracuda, Asus, TP-Link and it seems to have gone even further, partnering with the INTERPOL.
So, it’s pretty much clear that your data is most likely going to be used for security-related practices and less likely for ads or anything of the sorts.
How to stop Trend Micro from receiving my data?
The easiest way is by not agreeing to use their software, but, if you already enabled the AiProtection, it’s fairly easy to stop sending data.
Open the Asus web-based interface and then go to Administration > Privacy and then simply click Withdraw from under the Trend Micro section (the second). Be aware that disabling them, will affect the functionality of the AiProtection, as well as the Traffic Analyzer, the Apps analyzer, the Adaptive QoS / Game Boost and the Web history. This means that you’re going to be left with a severely crippled router, which is why it’s best to understand what the router does before purchasing it.
What alternatives are there to Trend Micro’s AiProtection?
As I mentioned before, you don’t have to configure anything when you use the AiProtection and the most that you can do is enable or disable one of the four available features, so there aren’t any alternatives that are as simple to use and that work in a similar manner. Of course, there is SNORT, Suricata and other similar software available, but you will need far more powerful hardware (a computer is ideal, but there are some enclosures available that you can purchase) and it’s not going to be easy to configure or maintain. Obviously, if you are either very ambitious or have the technical know-how, these open-source software are clearly superior.

Mark is a graduate in Computer Science, having gathered valuable experience over the years working in IT as a programmer. Mark is also the main tech writer for MBReviews.com, covering not only his passion, the networking devices, but also other cool electronic gadgets that you may find useful for your every day life.


Mark,
I am replacing an old router with the ASUS AX56U. Your reviews have been very helpful in helping me to decide on the AX56U. In looking at the Ai-Protection information in this article I noticed that “Personal information contained within email content or files to which Trend Micro is provided access. Storage of emails for back up purposes (certain cloud products)”. Does this mean that Trend Micro would have access to all my e-mails and their content? I wasn’t planning to disable Ai-Protection but I was somewhat concerned about this. I appreciate your thoughts and suggestions. Thanks.
Mark,
I am migrating from an old router to the ASUS 56U. All of your reviews have been very helpful in evaluating many routers.
Looking at all the information that Trend Micro collects, I noticed “Personal information contained within email content or files to which Trend Micro is provided access
Storage of emails for back up purposes (certain cloud products)”. Does this mean that they have access for all e-mails and their content? I was not planning to disable AiProtection but was concerned about this aspect of the privacy protection.
Would appreciate your thoughts and advice. Thanks.
This is a great question and after checking out Trend Micro’s website I came across this: https://success.trendmicro.com/solution/1120463. In my opinion, the Disclosure is a bit more general and covers multiple services that Trend Micro offers. So, I think that TM accesses the emails only if the user uses a specific service (such as the enterprise security suite) and it’s not something that they do with Asus routers. I have had an Asus router block a specific malicious website, but I never gotten any message when I attempted to open malicious emails (and I do get hundreds of them on a daily basis). Hope this helps.
Thanks for responding so quickly. So it seems that e-Mail privacy is not an issue with AiProtection and it is beneficial to take advantage of the TM security feature and not disable it.
.
One additional question on the AX56U. I currently do not have any WIFI 6 devices. When I install the router to I need to change any WIFI settings to account for my WIFI 5 devices? Thanks again.
No, you don’t have to adjust anything, Asus has set the wireless networks in mixed mode (802.11ac and 802.11ax) by default, so both WiFi 5 and WiFi 6 devices can connect at the same time without problems.
Asus (Asustek) is a Taiwanese company, not Chinese.
Thanks for pointing it out. I corrected it in the article.
This is a great article Mark, very clear. Thank you very much.
Do you know if the “HomeCare” feature that is available in TP-Link routers, and which is also powered by Trend Micro, also “calls home” like AiProtection from ASUS does? Or does it just download from the Trend Micro cloud some rules that it applies locally, without leaking personal data to Trend Micro?
I am currently deciding between buying a TP-Link router or an Asus router, without good privacy I am not sure that a security feature is valuable for me…
Trend Micro works essentially the same with all routers that it has partnered with, so it shouldn’t differ from one brand to the other (be it TP-Link or Asus) – the data collection is the same. As for HomeCare, be aware that not all new TP-Link routers come with this security package, since the manufacturer decided it’s better to slowly migrate towards the subscription-based Home Shield (powered by Avira, if I remember correctly).
Thanks a lot for your quick reply!
I was looking at a TP-Link router released in summer 2019, so not so old.
If there’s no difference between TP-Link HomeCare and Asus AiProtection in regards to privacy, then at least Asus has to be commended for showing a warning. I am not sure if TP-Link does it; at least, I’ve not read about it in any review of the said TP-Link router (and I’ve read quite a few).