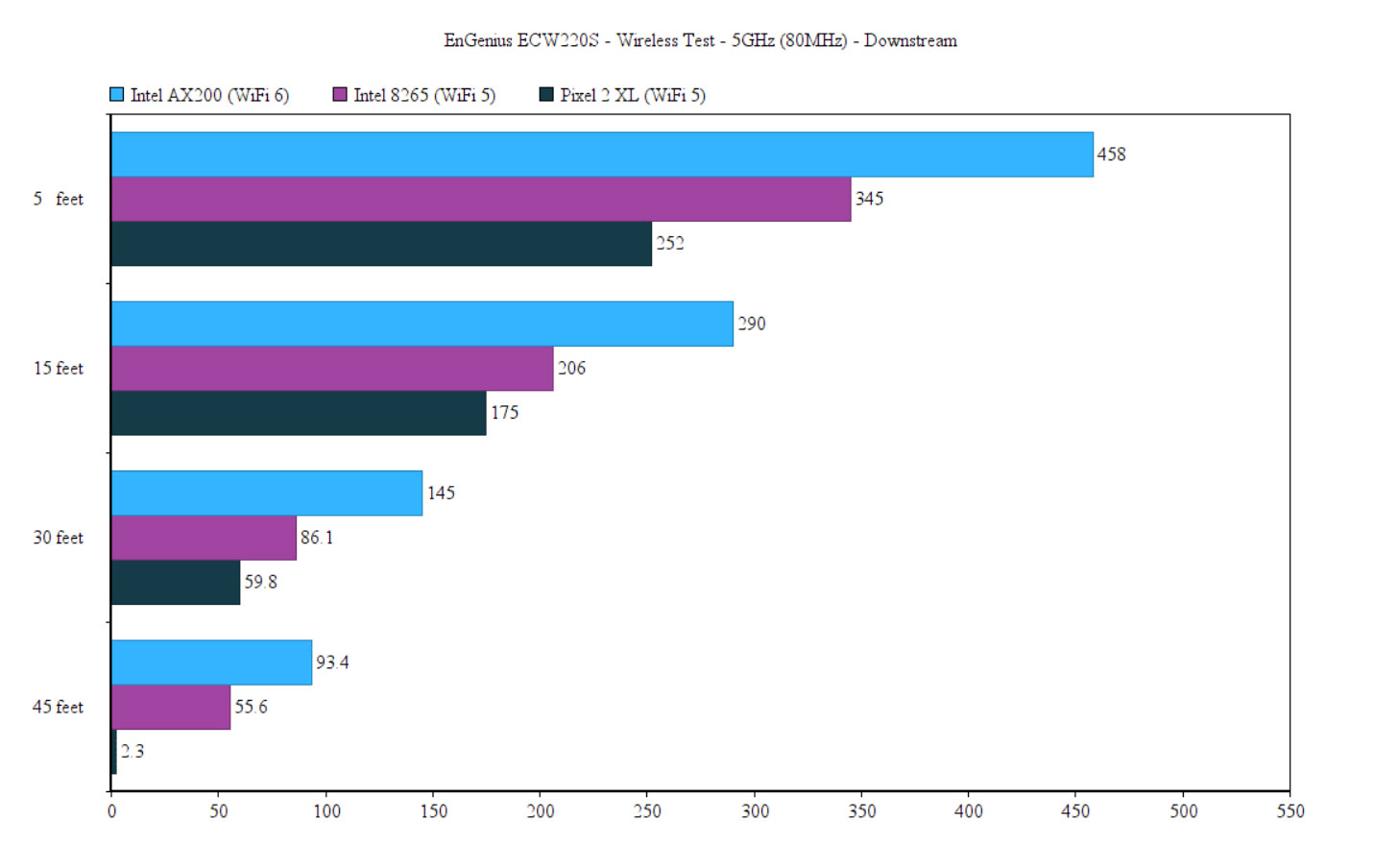
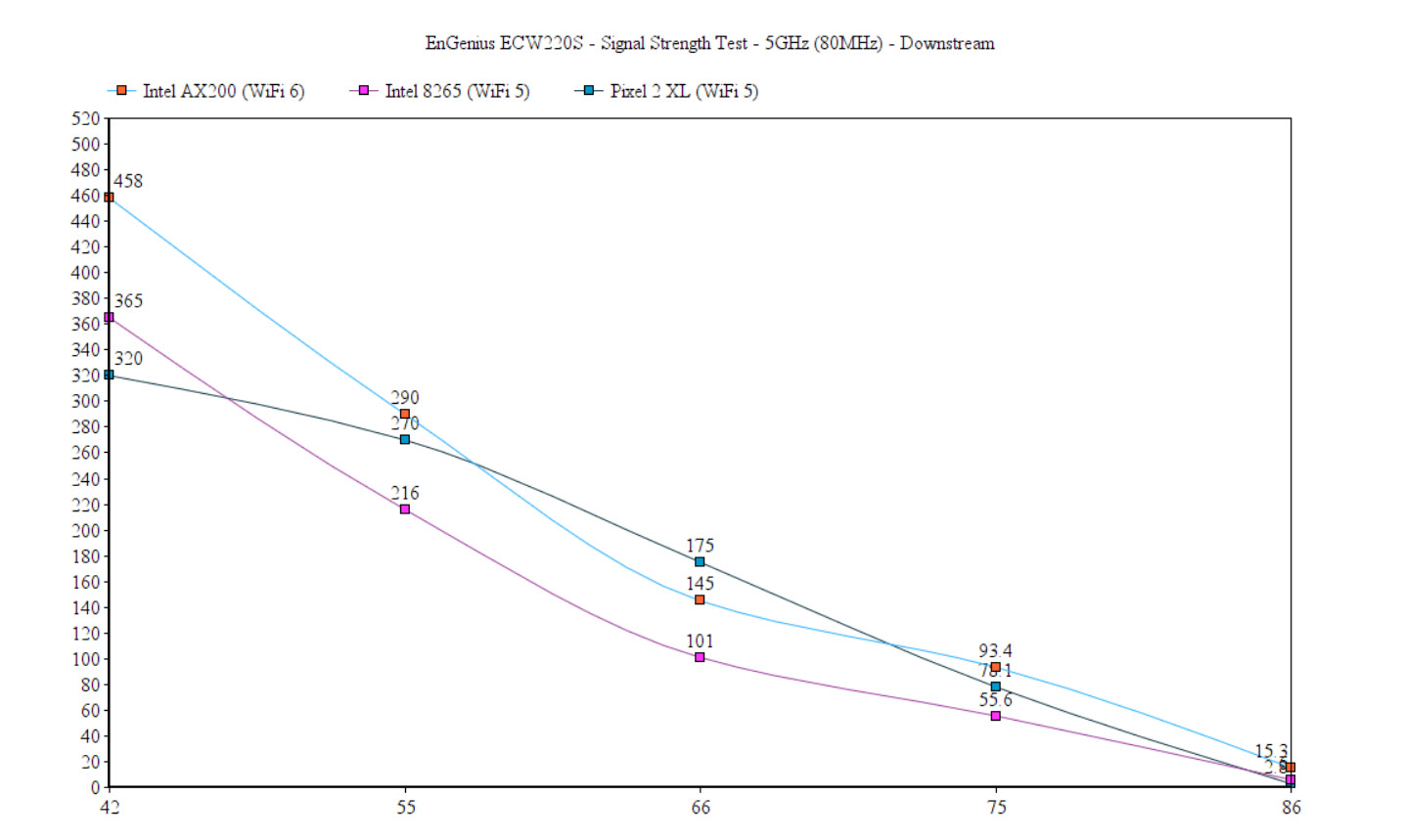
This way, I saw an average of 557Mbps at 5 feet (-44dB), 307Mbps at 15 feet (-53 -again, a better performance than the ECW220) and 112Mbps at 45 feet. The throughput became unusable when the signal reached -88dB, when it was an average of 7.7Mbps. Downstream, I saw an average of 345Mbps at 5 feet and an average of 55.6Mbps at 45 feet. Lastly, I took a mobile phone (Pixel 2 XL – WiFi 5) and ran the same tests: this way, upstream, I got an average of 293Mbps at 5 feet and 59.8Mbps at 30 feet – at 45 feet, it became unusable (2.8Mbps, -87dB).
Note: it does take the access point quite a bit before broadcasting the signal (up to 5 minutes).
Wireless Test (2.4GHz)
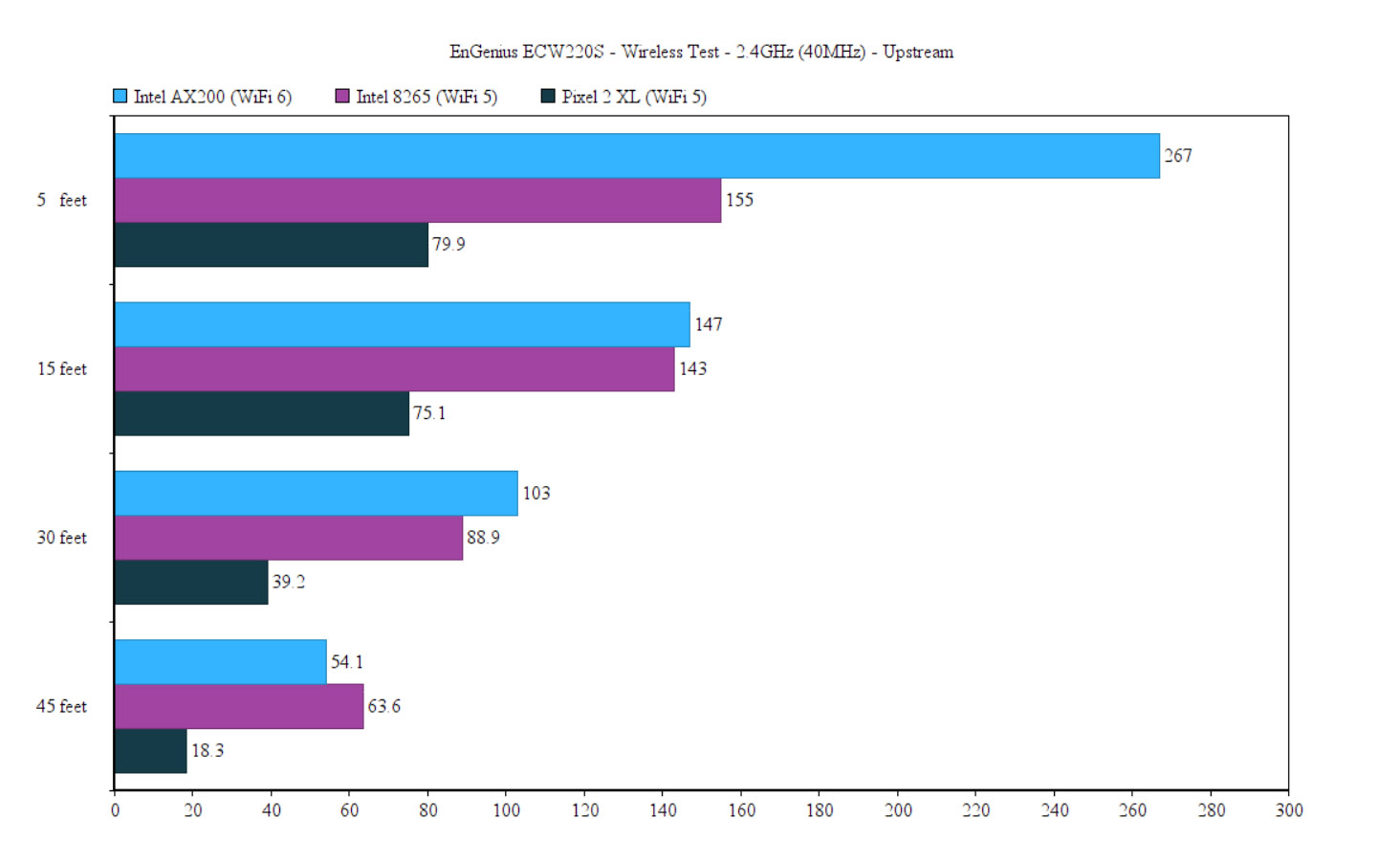
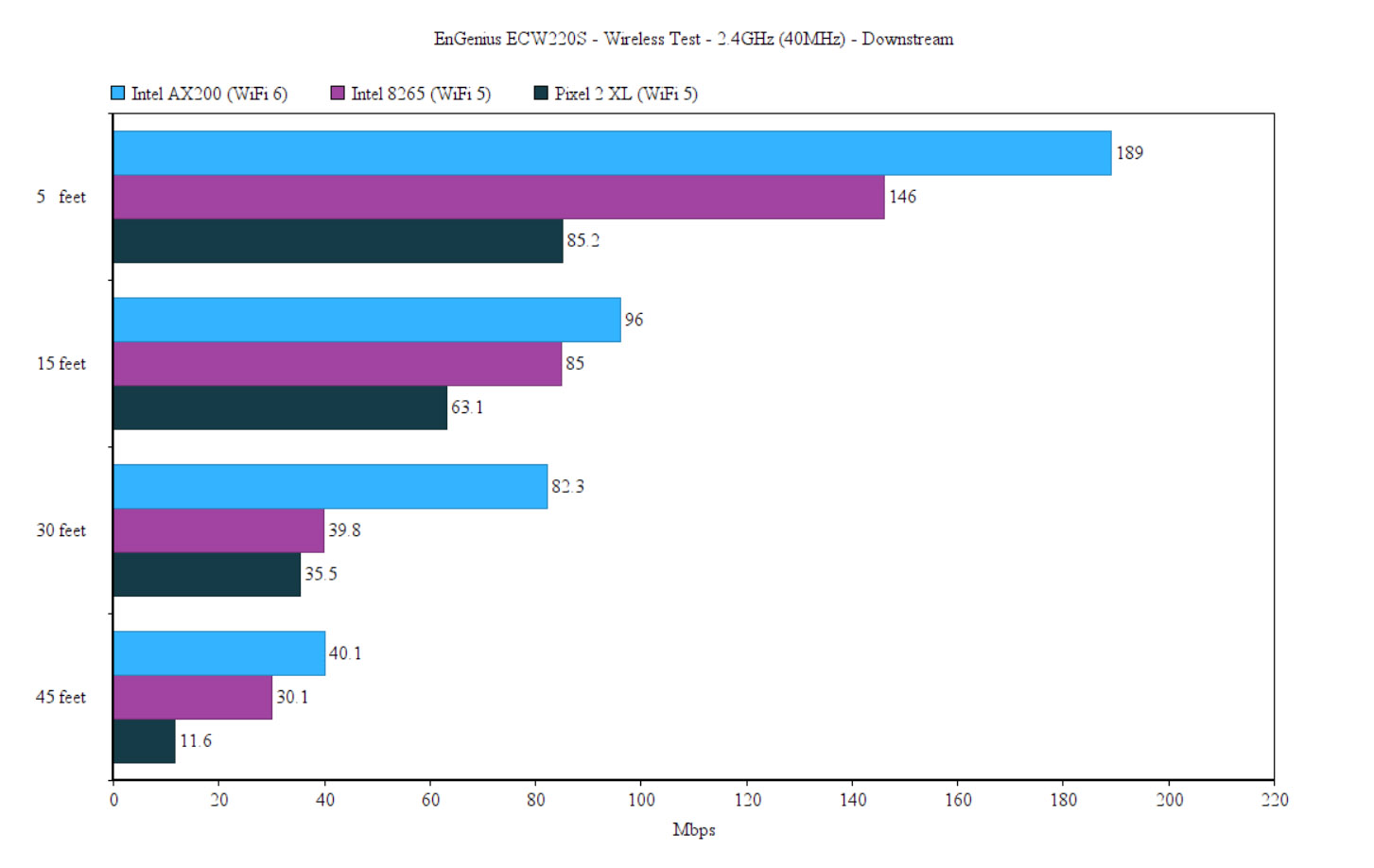
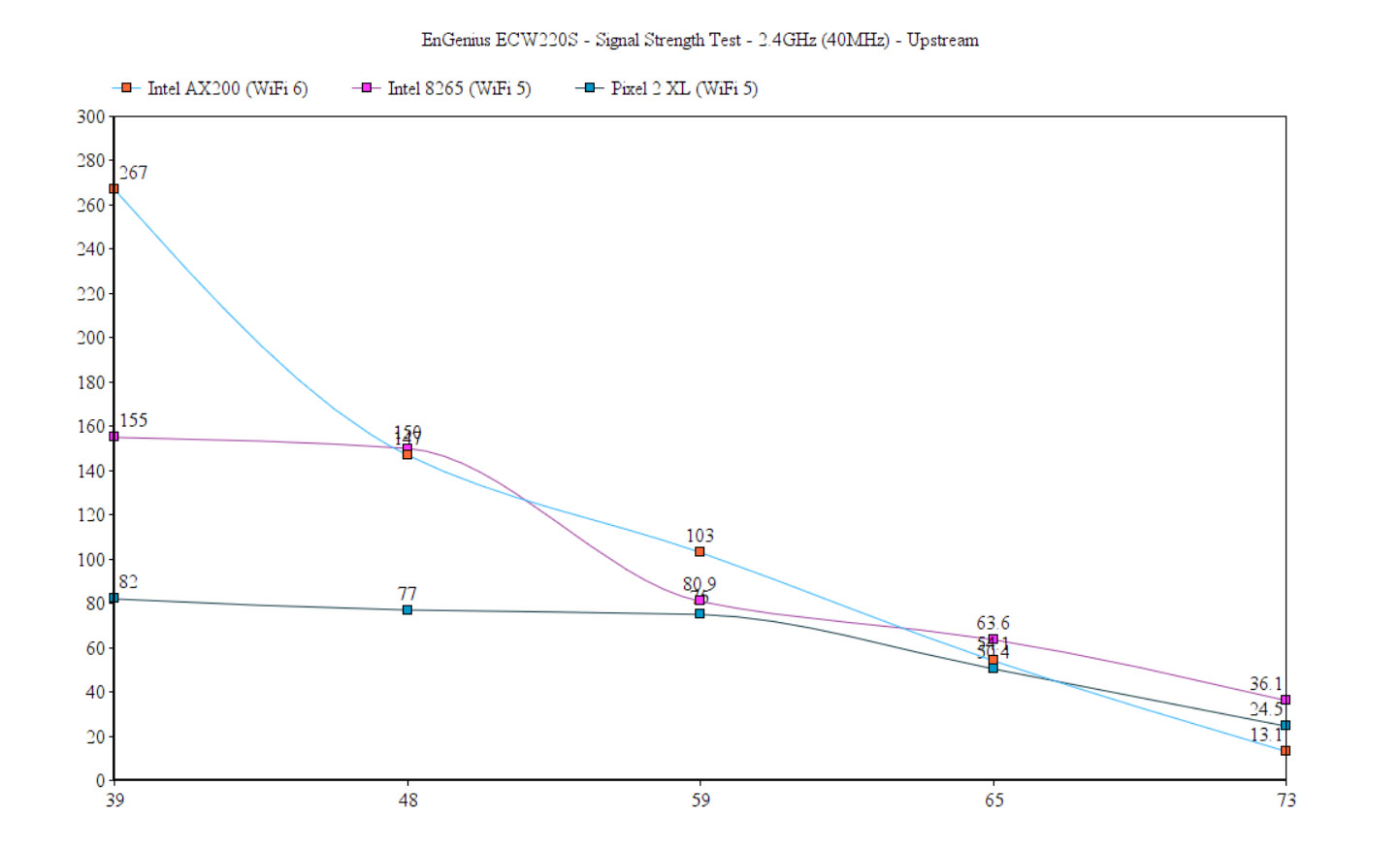
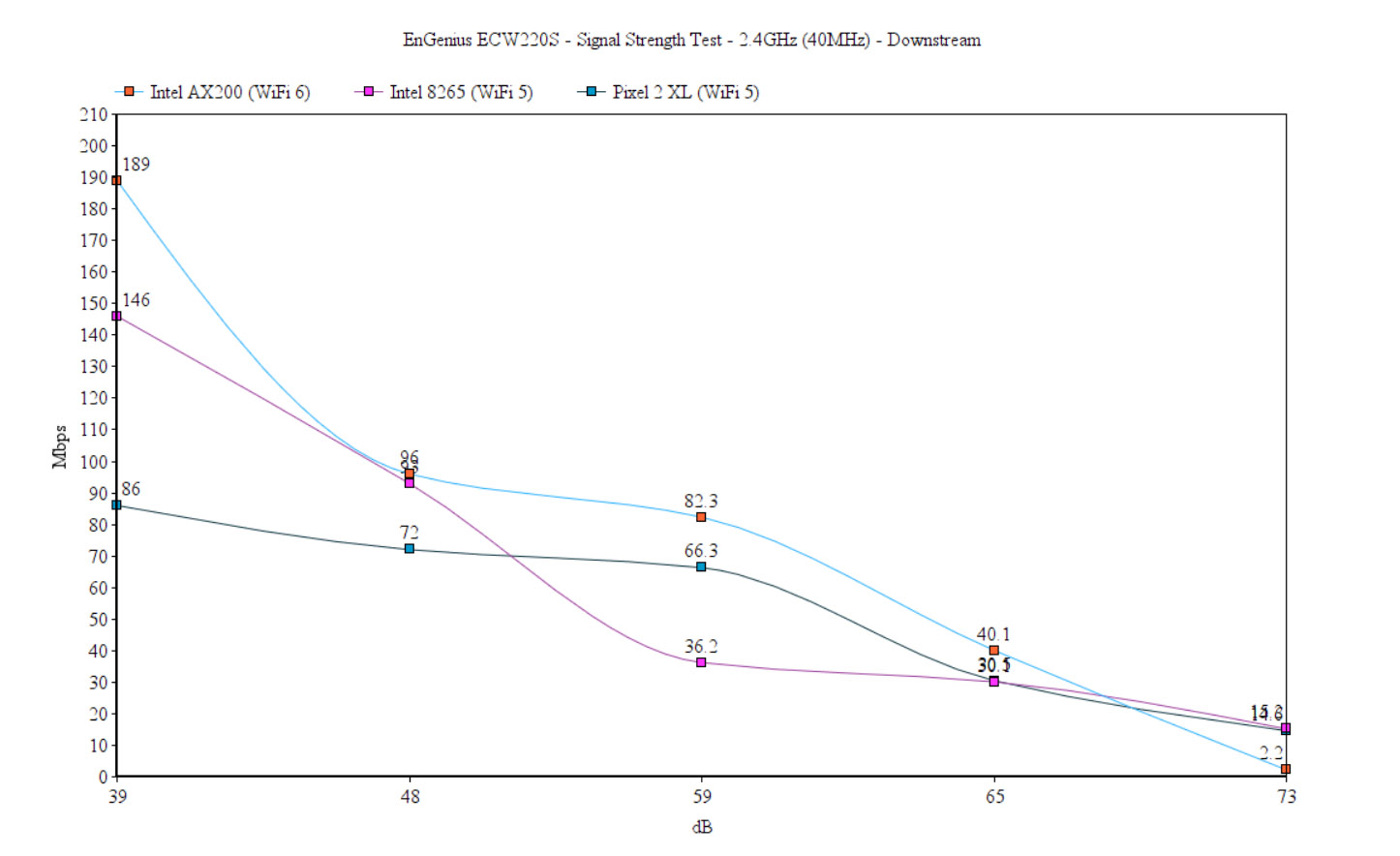
As you will see, the AX200 client device showed a slightly lower throughput at 5 feet, but the performance overall remained pretty much in line with what we saw with the EnGenius ECW220. That being said, while the Intel AX200 client device was connected to the EnGenius ECW220S (2.4GHz network), I saw an average of 267Mbps at 5 feet (upstream) and 54.1Mbps at 45 feet. Downstream, at 5 feet, I measured an average of 189Mbps and an average of 40.1Mbps at 45 feet. It’s worth mentioning that, at about 65-70 feet, the signal was on average -73dB and the throughput was barely usable (13.1Mbps up and 2.2Mbps downstream).
Moving on to the Intel 8265 WiFi 5 client, I got an average of 155 Mbps at 5 feet (upstream) and an average of 63.6Mbps at 45 feet. Downstream, I saw an average of 146 Mbps at 5 feet and 30.1Mbps at 45 feet. It’s interesting to see that the even if the signal strength was the same as with the Intel AX200 (-73dB), the throughput was entirely different: 36.1Mbps upstream at about 70 feet and 15.2Mbps downstream. Still very much usable. The WiFi 6 smartphone client was fairly decent, although nothing impressive.
Upstream, at 5 feet, I saw an average of 79.9Mbps and at 45 feet, it went down to 18.3Mbps (it did not go farther than that). Downstream, it was 85.2Mbps at 5 feet and 11.6Mbps at 45 feet.
Setup and Software
Since the entire installation process is pretty much identical to the ECW220, know that there’s a stand-alone GUI which doesn’t offer that much in terms of features, but it will still work and connect to your client devices. I would not recommend getting the EnGenius ECW220S unless you plan to use the Cloud platform, since the price is not going to be justified otherwise. The pairing process to the Cloud is also identical to the ECW220 and the ECW230, so you either use the app (and scan the QR code) or simply insert the Serial Number manually – to register the device (Organization > Inventory and Licenses).
Then, simply assign the device to a Network. We also need to talk about the License which you will need to assign to the newly added ECW220S and yes, you do get 1 year Pro license for free. Afterwards, you will have to purchase the license, otherwise, some of the advanced features will not work. The Cloud platform interface doesn’t seem to have changed from when I tested the other wireless access points, so you can read a more in-depth dive when I check out the ECW220 and the ECW230. And, for now, let’s see what’s new with the EnGenius ECW220S.
What’s new?
First of all be aware that most of the security features are only available with the Pro license (for example, the Network Activities under the Diag tool will remain available only for a minute at a time on the basic license). That being said, there are quite a few new elements.
1. Diagnostics
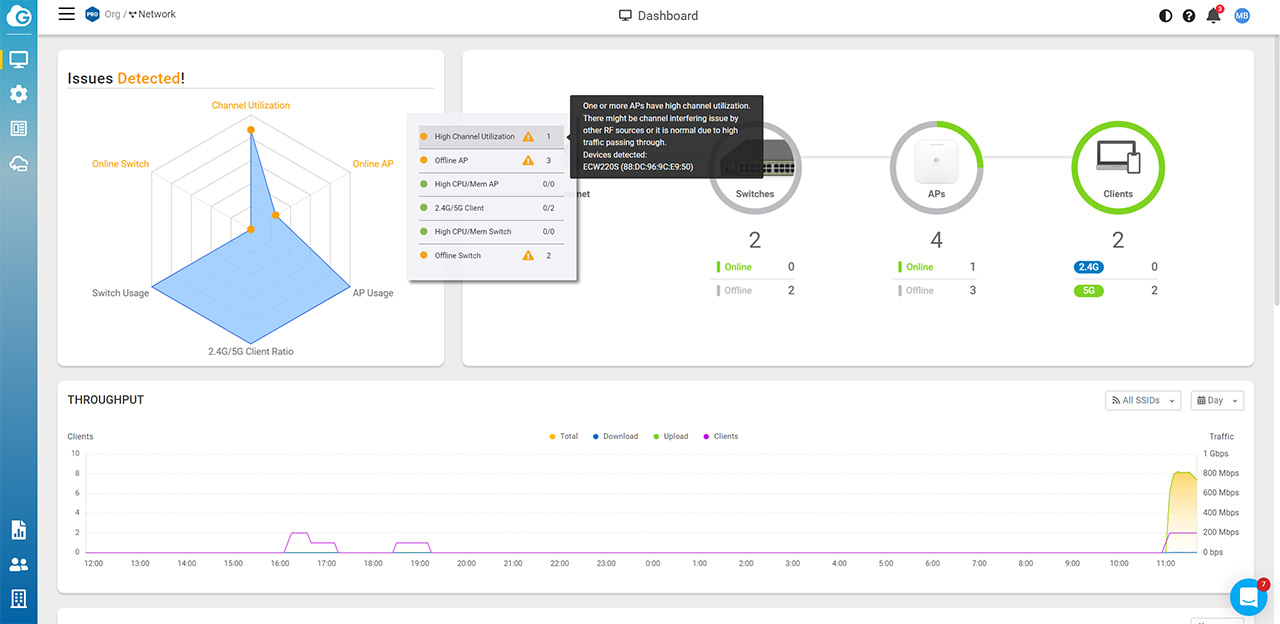
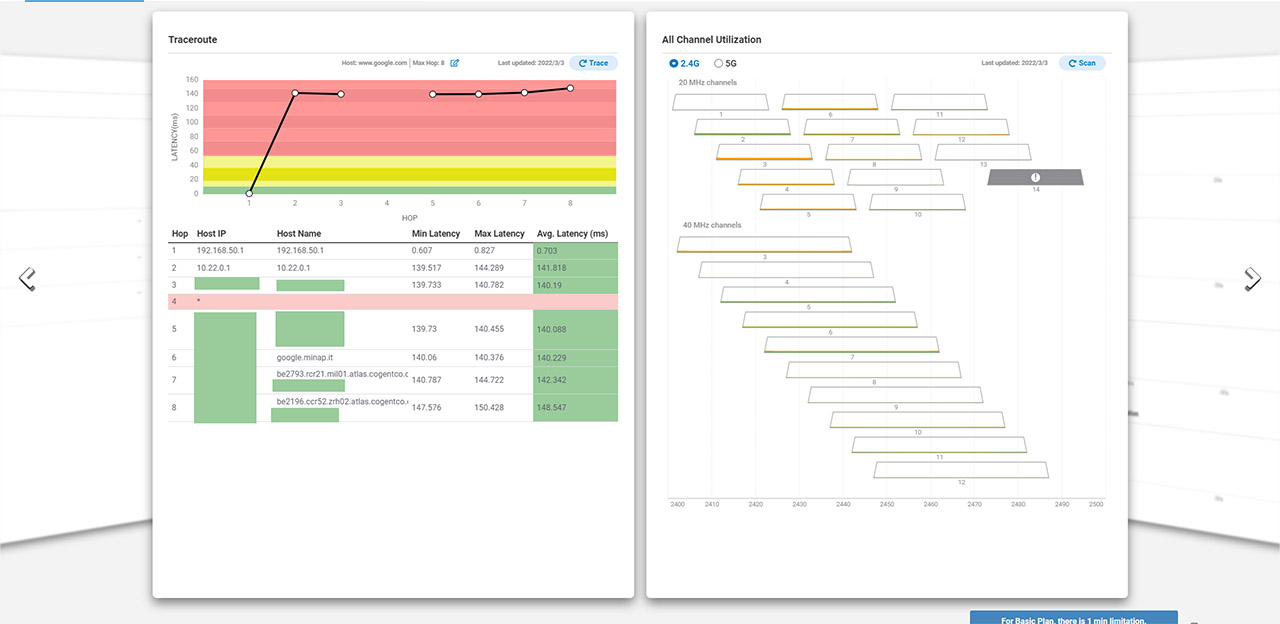
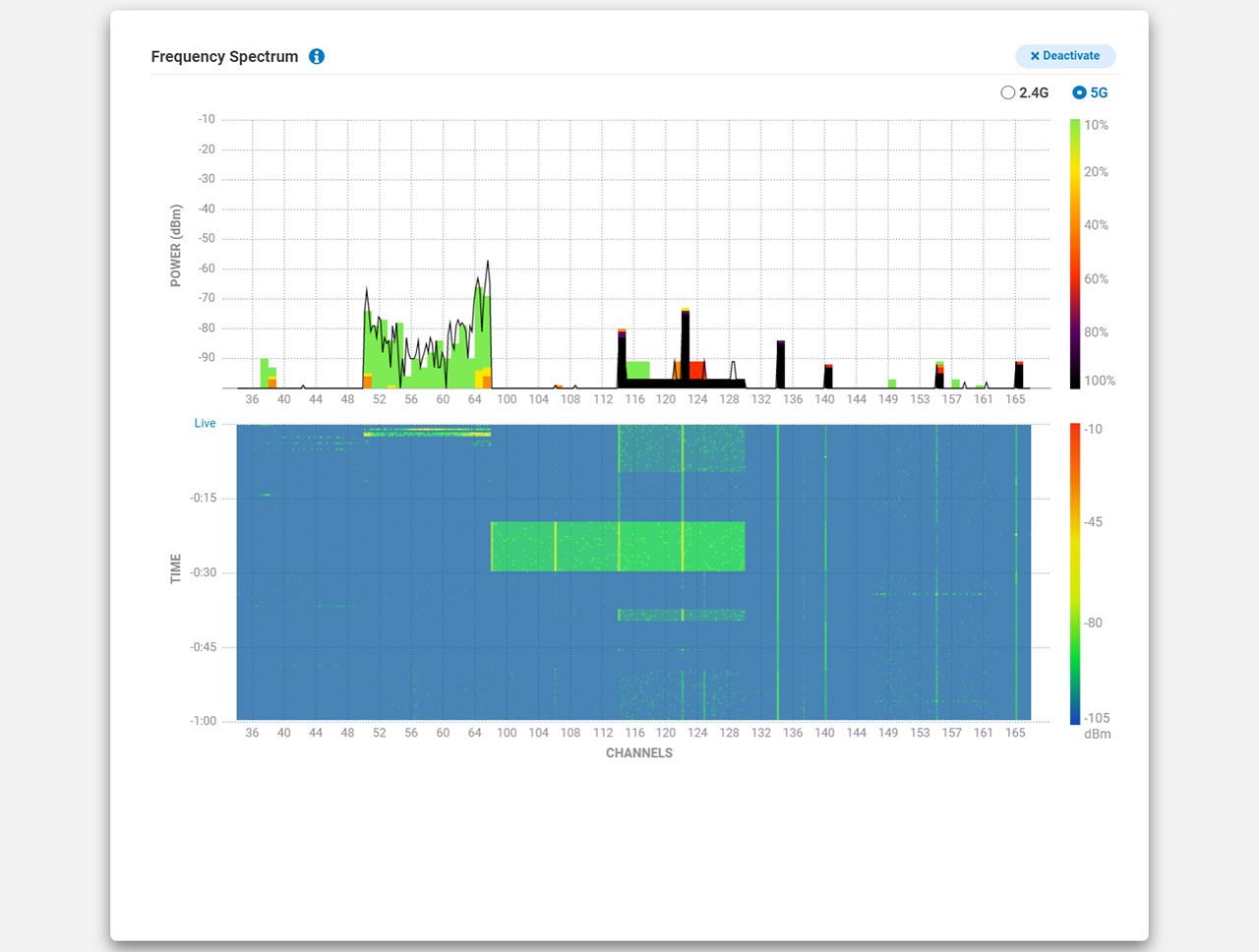
The first one is the Diag tool which is going to appear next to the access point when you hover the mouse over it. Click on it and you will be taken to a dedicated window which is going to be divided into three tabs: Network Activities, Spectrum and Live Clients. The Network Activities will show the live activity of the access point, including the CPU, Memory, Throughput and Channel Utilization. Then, you can see a continuous ping towards some major websites, but you can add your own and a very interesting Traceroute representation. You can see the number of hops (including the IP and latency) for the aforementioned websites (you can check your own as well). Lastly, there’s the Channel Utilization which scans for all the available channels and let’s you know how much of it is being utilized.
As you can see, almost nobody is using the 80MHz channel bandwidth in my area, most simply crowding the 20MHz one for both 2.4GHz and the 5GHz bands. The Spectrum tab will essentially show the amount of interference you can get on each channel, including the Bluetooth signal. The Live Clients section doesn’t mess around because the second I connected a phone, it appeared in the list – yes, it’s that fast. All these tools are incredibly useful for system admins to detect if the clients are actually connected, when and to which channel are connected. Also, it helps see what’s going on in real-time, including interference and it will help solve any issues remotely, without having to constantly go on site.
Note: When you run a scan, be aware that it will disrupt the client (will go offline if it can’t connect to any nearby AP).
2. AirGuard
The second feature is the AirGuard suite of security tools which include Rules, Rogue SSIDs, Other SSIDs, Evil Twins, Malicious Attacks and RJ Jamming. Under Rules, you can add specific APs to the block or whitelist and then you can view the Rogue SSIDs in the next section. I didn’t have any devices that fit the characteristics of a rogue AP (which is great), so the list is empty. Still, the Rogue SSD information will give you a good idea about where the device is located since most likely can be detected by multiple APs, each showing the signal strength of the rogue AP. Furthermore, the EnGenius ECW220S will show all the other SSIDs in the vicinity, a tool that I saw on other APs as well (such as Ubiquiti UAP-AC-PRO) and it will also show a list of all the devices that can perform an Evil Twin attack.
The interesting thing is that the EnGenius ECW220S is quite good at detecting the AP Impersonation technique which not only copies the SSID name, but also the MAC address, making it far harder to tell apart from genuine access points in your network. The last two sections show any Malicious Attacks (DoS attacks) that have been conducted and, under RJ Jamming, you can see if the ECW220S has detected any type of jammer in the vicinity of the AP.
The Conclusion
The EnGenius ECW220S’ entire reason of existence revolves around the Bluetooth antenna and the extra radio dedicated for scanning the area for both potentially harmful devices and for getting a better idea on how the network can be improved. And it’s definitely a step up from the ECW220 even if it has so many common elements with the ECW220S. It’s so much easier for sys admins to troubleshoot any problems that may arise without needing to go on the site. And EnGenius has done a really good job at using the extra hardware for detecting rogue APs and other type of intrusive practices that can seriously harm the network performance, as well as expose sensitive data. So, in my opinion, the (Apple-esque) S at the end of the name is very much justified since the EnGenius ECW220S can’t really be considered a part of a completely new generation of APs, but, at the same time, it does have enough improvements to justify it’s place alongside the other ECW access points.

Mark is a graduate in Computer Science, having gathered valuable experience over the years working in IT as a programmer. Mark is also the main tech writer for MBReviews.com, covering not only his passion, the networking devices, but also other cool electronic gadgets that you may find useful for your every day life.