The Client VPN section allows the user to use IPsec only, for now and it’s very easy to configure. Lastly, there’s the Firewall, where you can set Outbound Rules (TCP, UDP, ICMP or Any), Port Forwarding (either WAN or both WAN1 and WAN2), add 1:1 NAT rules, as well as edit the Allowed Services (ICMP Ping and Web config). For now, these seem to be the main features and settings, so let’s have a look at some of them a bit more in detail.
Dual-WAN Configuration and Test
EnGenius has made the dual-WAN configuration very simple and easy to understand, but it is also a bit more limited in options than other multi-WAN gateways out there, including the TP-Link TL-ER7206. Each of the two WAN ports supports DHCP, PPPoE and Static IP connections, it’s possible to choose the DNS Server, set a VLAN ID and limit the bandwidth.
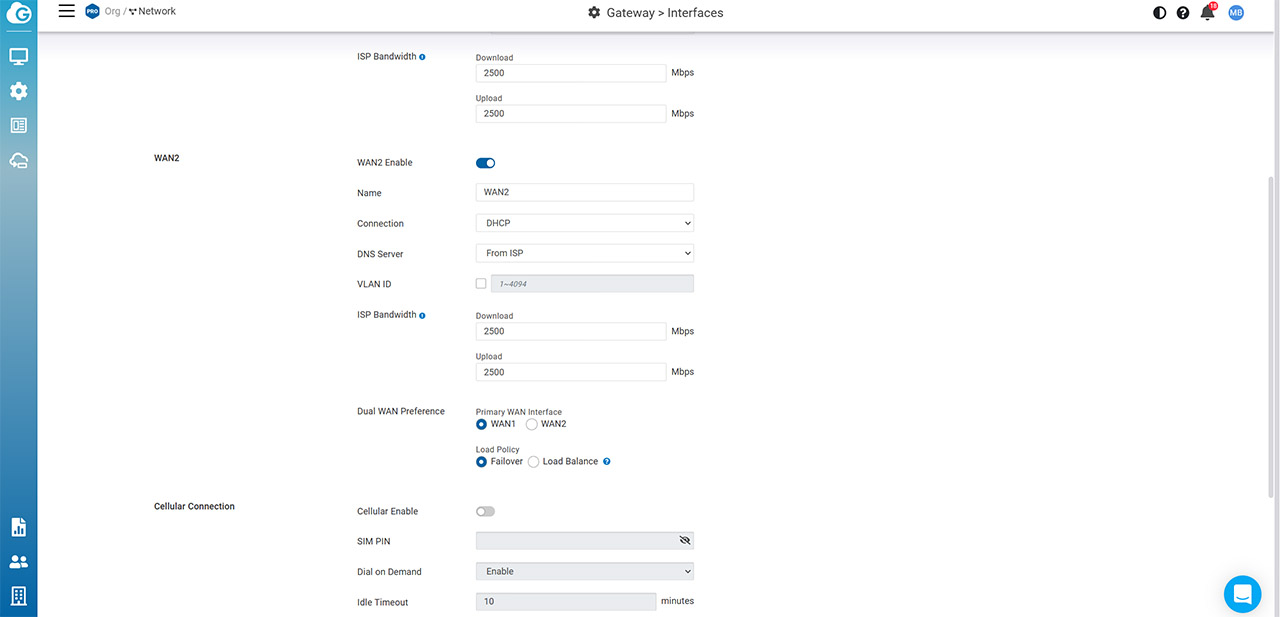
You can also choose the Primary WAN Interface, so, when selecting the Failover policy, when the link returns to the primary WAN, the gateway will switch back automatically to that port. Before moving forward, I decided to check out just how quickly the EnGenius ESG510 is able to switch from one WAN to the other when set up in Failover mode. So far, almost all dual-WAN routers that I tested managed to perform this switch in about a second.
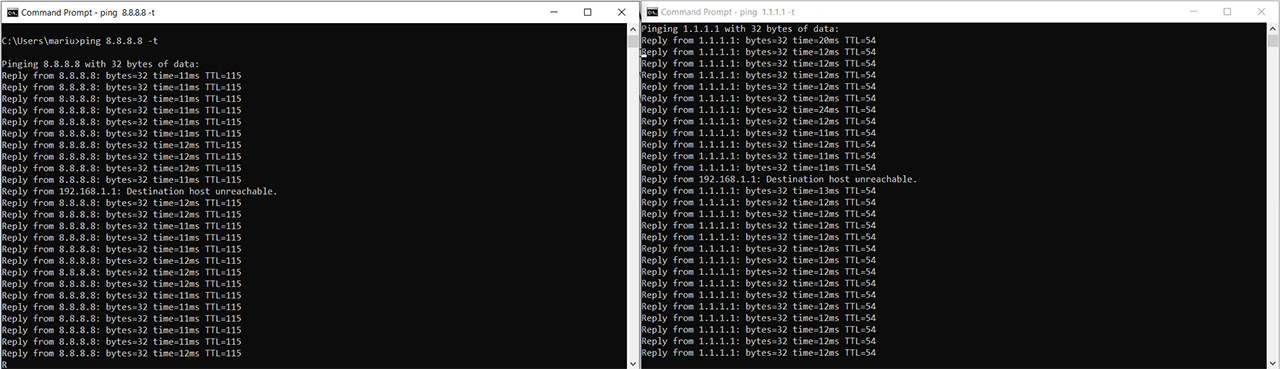
I connected the gateway to two separate routers and while both were connected to the ESG510 (WAN1 primary and WAN2 secondary), I ran two concurrent Ping tests to 8.8.8.8 and 1.1.1.1. After that I disconnected the cable from the WAN1 port. As can be seen from the screenshot, there is a single ‘Destination host unreachable’ message which means that only one packet was lost during the switch. I redid the test several times and every time I got the same result. Next, I decided to see how long does the EnGenius ESG510 needs to return to the WAN1 port which was set as primary.
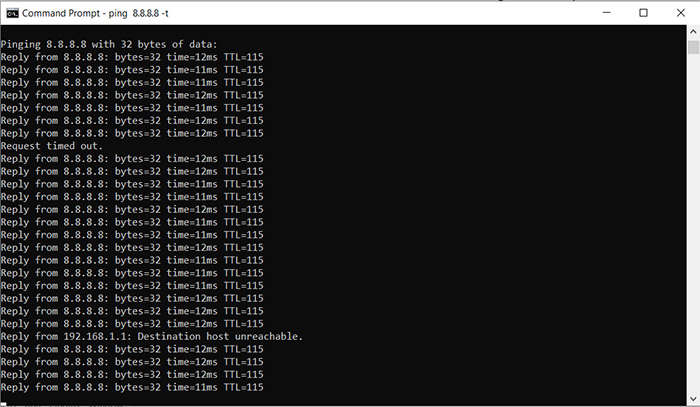
I tried it several times until the switch was done seamlessly after about 9 seconds. What that means is that after the link returns to the WAN1 port (in my case, I reconnected the cable), the gateway will take about 9 seconds to switch back to it. Besides the Failover policy, it’s also possible to use the Load Balance mode which essentially enables the WRR or weighted round robin and it’s a way to divide the load between the links.
At the moment, you can’t select the weight (although I assume setting a primary WAN will give it more weight) and, at least for now, there is no support for link aggregation. About the Cellular Connection, you can set it up by entering the SIM PIN, the Idle Timeout and the Dial on Demand.
The VPN Configuration (IPsec)
As I have previously mentioned, the EnGenius ESG510 supports IPsec Client VPN and the developers did say that more types will be supported in the future. And to set it up, you need to go to Configure > Gateway > Client VPN and enable it, then choose IPsec which is for now, the only available.
Then, take note of the Hostname, choose a VPN Client Subnet (a subnet that’s not used anywhere else on the network), choose the DNS and the WINS Serves (I left the default ones) and then, I entered a Pre-Shared Key (again, take note of the key because you will need to use it again).
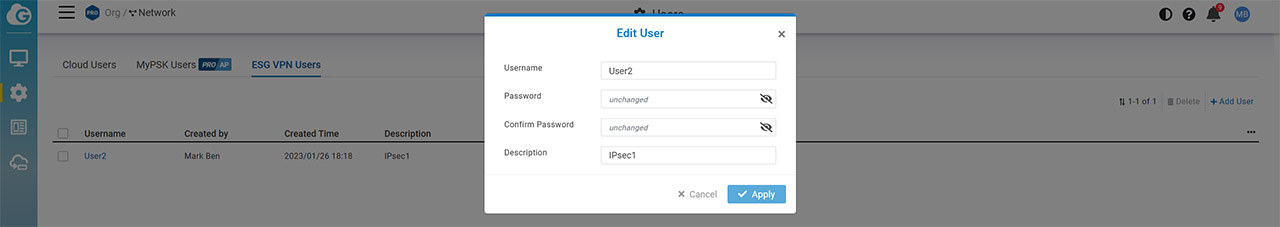
Afterwards, I had to create a VPN username. This can be done by going to Configure > Users > ESG VPN Users. Here, you need to set up the username and password. Then, I decided to use an iOS device since I had the IPsec profile already created from since I tested the TP-Link TL-ER7206. The idea is to set the Server to the Hostname written on the ESG510 config page, insert the Account name and Password, as well as the Secret (the passkey that we previously set). That’s about it.
The Conclusion
Considering that the EnGenius ESG510 is the first gateway developed by the manufacturer, it did manage to get a lot of things right. The dual-WAN support is fairly well rounded and the extra 3G/4G/5G dongle support is a welcomed addition. The stars of the show are the four 2.5GbE ports, including a PoE+ one and I hope this is a trend that many other brands will follow suit (without going out of control with the pricing). Also, the integration with the Cloud management platform is so far, well done.

At the same time, I can’t help feeling that we need more. I am aware that more VPN-related features will come to the ESG510 (hopefully some of them not locked behind a subscription), but the developers absolutely need to add some IPS/IDS implementation (specific to the gateway, not just under the pro feature AirGuard). And I know that this will have an impact on the throughput (which is pretty much unaffected by any of the current features right now), but I am fairly sure that the hardware can handle it (this exact platform works great with pfSense which is far more demanding).

Mark is a graduate in Computer Science, having gathered valuable experience over the years working in IT as a programmer. Mark is also the main tech writer for MBReviews.com, covering not only his passion, the networking devices, but also other cool electronic gadgets that you may find useful for your every day life.

