The Zyxel NSG50 is a part of the managed security gateway series and it’s the final piece towards a complete Nebula Cloud network solution, designated for routing purposes, connecting the internal network consisting of other Zyxel access points or Ethernet switches (and not only) to the outside network (so, essentially, it will work as a router).
The security gateway wasn’t built for the consumer market since most of its features are beyond what the regular user would need for a home network (although, if you value the security of your network, it’s worth giving it a try). But, the SMBs (and possibly the corporate market) will appreciate its advanced applications which includes Firewall, multi-WAN, VPN and other security-related features (such as the Antivirus, IDP or Content Filtering).
Zyxel NSG50 goes one step further and, unlike the regular security gateways, it doesn’t require on-site provisioning, so it can be managed and configured remotely from the Nebula Cloud (out of the box), along with other Zyxel security gateways or other compatible devices. I have already seen the Nebula Cloud management platform in action when I tested the Zyxel NWA1123-AC HD wireless access point and the Zyxel GS1920-8HP Ethernet switch, so it’s time to see if the security gateways are properly integrated and if the Zyxel NSG50 can outclass its competitors in terms of features and performance.
Note: Besides the NSG50, Zyxel also offer more powerful solutions such as the NSG100, NSG200 and the NSG300 – none have built-in WiFi capabilities.
Design
Similarly to most non-consumer networking hardware, the security gateway was built to either be mounted on a rack or to be tucked away somewhere in a closet, so an attractive design wasn’t the main focus and the manufacturers instead targeted the functionality and the ergonomics.
The Zyxel NSG50 adopts this form follows function principle, fully embracing the industrial look, so it features a rectangular metallic case with sharp corners and it’s covered by a gray matte finish which does not retain fingerprints (if the gateway was ever intended towards the consumer market, the more unique design of the DrayTek Vigor2926 is probably going to be more appealing, even if it’s completely made of plastic). On the front, the device is very similar to the gateways from the USG series, so it has a plastic piece with two protruded areas, but instead of them being red, the NSG50 went with white tones (and this is going to be one of the main differentiating design element between the two Zyxel series).
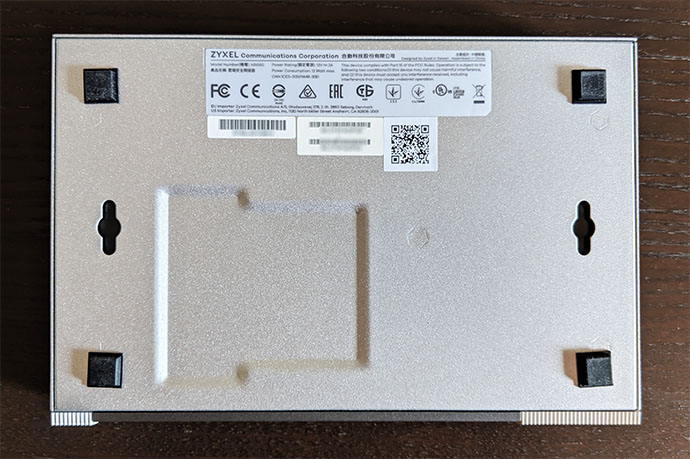
The Zyxel NSG50 is the most compact Nebula Cloud security gateway, measuring 8.50 x 5.63 x 1.30 inches, so it’s actually smaller than your regular wireless router, which also means that it won’t occupy too much space from your desk. If you want to mount it on a rack, you will have to rely on a tray since the gateway doesn’t have any dedicated holes on the left and right side of the case, but you do get the option to mount it on the wall by using the two areas on the bottom of the device. On the top of the Zyxel NSG50, there are six rows of ventilation cut-outs to ensure a proper internal airflow and the manufacturer has also added two sets of ventilation grills on the left and right side of the case. While the device was running, I did notice that it got warm on the bottom area, but it didn’t show any signs of overheating, even when it was under stress.
The bottom of the gateway is devoid of any ventilation cut-outs, the only elements being the info labels and the mounting holes, so, if you want to keep the NSG50 on the desk, you need to add the four silicone feet (available in the package) which will do a decent job at keeping the device into place (the gateway is also quite lightweight, weighing only 3.11 lb). On the front panel, to the left, the NSG50 has a recessed Reset button (to return the device to the factory default settings, press and hold the button for about five seconds until the SYS LED started blinking), a PWR LED (if the LED is solid green, then the gateway is turned on and everything is working fine, but a solid red LED indicates a hardware component failure) and SYS LED (solid green indicates that the gateway is ready and functioning, but if the LED is flashing green, then the gateway is either booting, not yet registered to the Nebula controller or is searching for the NCC; a solid red LED indicates an error).
A bit to the right, there’s the P1 to P6 LEDs, each showing the status of their respective Ethernet port (flashing green indicates that data is being transmitted on that specific port and solid orange shows that the port has a successful link) and, lastly, there’s a USB 3.0 port (for now, it’s only useful for downloading diagnostic data, so you won’t be able to use it to push data between the clients and the external storage device, nor connect a printer).
On the rear side of the NSG50, there’s a 12V/2.0A power connector (it doesn’t have a large power brick), a On/Off button, an SFP port (to connect a transceiver – it can be used as the second WAN port to enable the FailOver mode), a Console port (useful for running terminal emulation communication applications – Zyxel provides a console cable inside the package), a WAN Gigabit Ethernet port and four LAN Gigabit Ethernet ports. Zyxel has also added a Kensington lock slot on the left side of the case, next to the ventilation grills.
Hardware
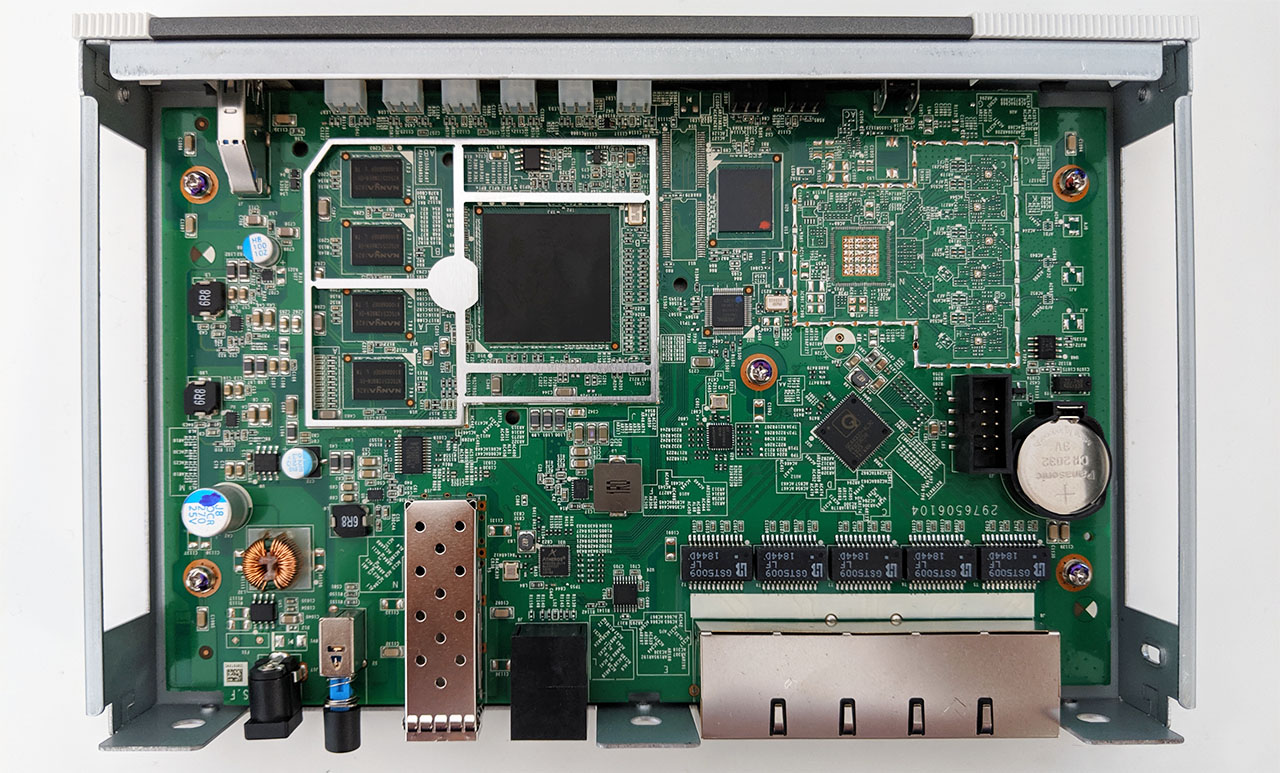
Inside the case, Zyxel has equipped the NSG50 security gateway with a single-core Cavium OCTEON III CN7010 embedded processor (clocked at 800 MHz), 4X 512GB DDR3 NANYA 1826 NT5CC512M8EN-EK (2GB of RAM), 8GB MLC flash memory from KINGSTON eMMC08G-M325 and a QCA8337-AL3C PK823C38 Ethernet switch.
Furthermore, there’s an Intel Altera 5M160Z CPLD, a Qualcomm Atheros AR8033-AL1A NJ836227 Ethernet chip (10/100/1000Mbps), a 24-pin NXP PCA9555 CMOS device and 5X GST5009 LF 1000 Base-T Magnetics Module.
Note: As with most security gateways, the Zyxel NSG50 does not have WiFi chipsets implemented, so, the only way to connect your wireless devices is to use additional wireless access points.
Features and Performance
All the Zyxel security gateways from the series have pretty much the same set of features (the differentiating elements mostly being the amount of clients that they can handle, the scalability factor and some applications’ depth), so the NSG50 will give you a similar experience to its more expensive siblings. Any small and medium businesses that need uninterrupted access to the Internet and can’t afford a single second of downtime will appreciate any routers that have dual-WAN capabilities and the Zyxel NSG50 does indeed support two independent Internet connections simultaneously, one through the designated WAN port and the other by using the SFP port (you will have to use an optical fiber link transceiver to create the second link).
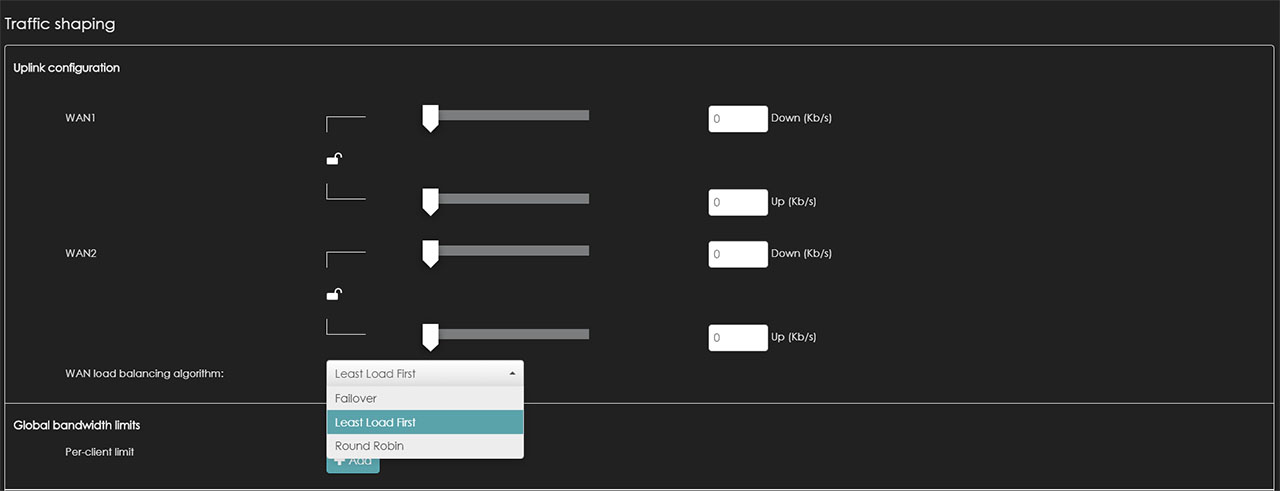
This way, you can visit the Gateway > Configure > Traffic shaping section from the Nebula Control Center and adjust various aspects of the Uplink configuration. The interface is very user friendly, allowing you to adjust the Download and Upload bandwidth for each WAN port (using a slide) and underneath, there’s the load balancing algorithm that will be applied. You can choose the Least Load First option which pushes a new session towards the most suitable WAN interface using the most recent inbound and/or outbound bandwidth utilization (the WAN connection with the least load will be assigned the new session), the Round Robin option which distributes the traffic through each of the two WAN connections in turn or the FailOver option which allows you to use the primary WAN and, in case the connection fails, it will automatically switch to the secondary WAN connection – in the meantime, the gateway will check if the main connection has returned and will once again switch to it from the secondary WAN.
For now, I didn’t have the means to test the latency when switching to the second WAN connection and vice-versa (I will update the article as soon as I test this feature). While the dual-WAN implementation is going to be enough for most users, in case you need a more in-depth configuration and more options, there is the Zyxel USG series (furthermore, the USG series, just like the DrayTek Vigor2926, it allows you to add 3G/4G/LTE modems to the load balancing pool). The USB port on the NSG50 can’t be used to connect external modems, but it can be used for external storage connection and, to test the storage performance of the gateway, I used a SanDisk Extreme SSD (250GB) formatted to the FAT32 format to move some data to and from the NSG50 (you can also use FAT16 drives, but NTFS is not supported).
Doing so, I went to the Nebula Control Center and happily checked for the storage options and … there were none. Yes, it seems that this feature is yet to be implemented, so I had to return to the stand-alone mode in order to see the drive. But not even in this case could I really test the storage performance because the drive is only to be used for the diagnostic data – still, under the Storage Information, I could see that the Speed was capped at 12Mbps and the USB drive was set at USB 1.1.
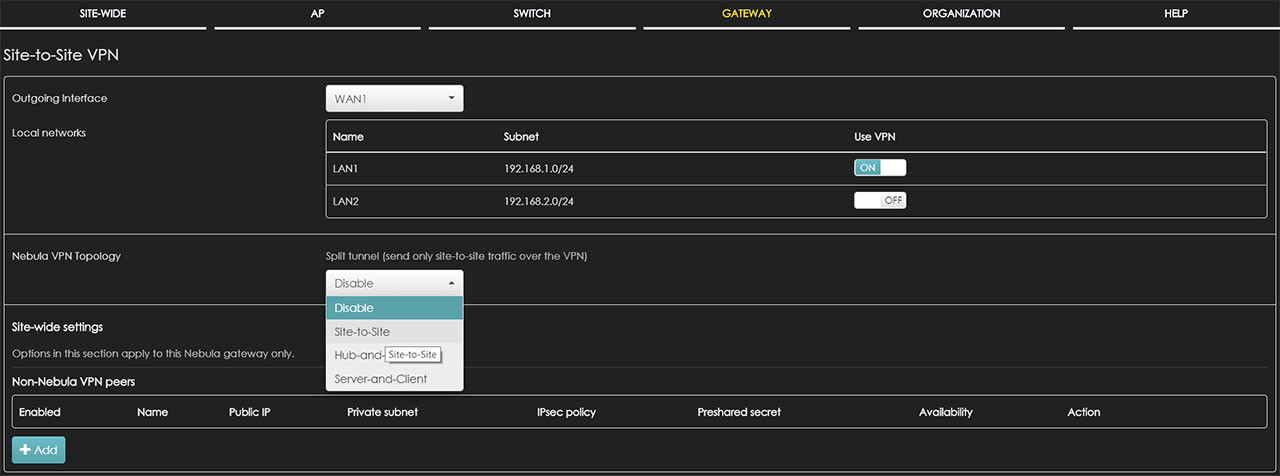
In terms of security features, the Zyxel NSG50 offers Site to Site VPN that can be applied to any of the two available outgoing interfaces (WAN 1 or 2) and it allows you to configure the Nebula VPN Topology (can be Site to Site, Hub-and-Spoke or Server-and-Client) – you can also add Non-Nebula VPN peers: I was quite surprised by the simplicity of the configuration process, rivaling the consumer-level routers in this respect. Furthermore, the gateway also supports L2TP over IPSec client, useful for creating a secure tunnel from your mobile devices to your LAN network.
Besides VPN, the NSG50 also supports Firewall (which includes Inbound and Outbound rules, Application Patrol and NAT/Virtual Server mappings), Antivirus and the Intrusion Detection and Prevention system (IDP) which supports behavior analysis and, based on layer 7 context-aware rules, it protects against both the server and the client side vulnerabilities, including malware, backdoor applications, DDOS attacks and more (the signature database is updated regularly to keep the network protected to any new threats).
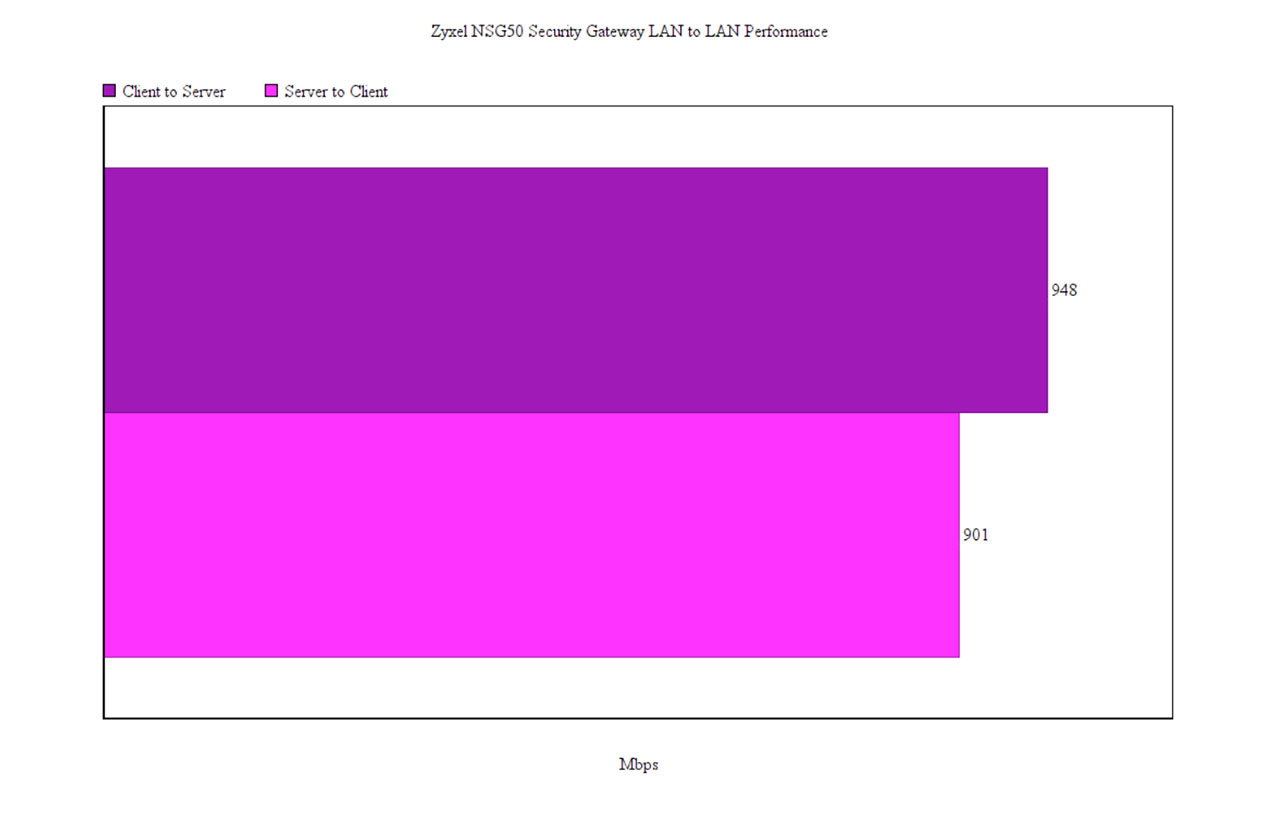
Considering that all these applications can have a negative impact on the throughput performance, I decided to connect two computers to the gateway using CAT6 cables and to test the LAN to LAN performance, first, without having any security features enabled: this way, from the client to the server, I measured an average of 948 Mbps and, from the server to the client, I measured an average of 901 Mbps.
Afterwards, I enabled the Application Patrol, the Content Filtering (which yes, apparently it can stop some ads and pop-ups!) and, with all these features enabled, I ran the test once again and, surprisingly, there was barely any difference (less than 5% degradation). When enabling the Intrusion Detection and Prevention (the system showed a 37% CPU usage and a 20% Memory usage), the throughput would fall at about 100Mbps (which is in line to what is advertised) – only the more powerful NSG300 can maintain a close-to-Gigabit performance. If I didn’t enable the IDP, but I ran the SPI firewall, I measured an average of 286 Mbps and the VPN throughput was also capped at no more than 70 Mbps.
Installation and Software
When I tested the Zyxel NWA1123-AC HD and the Zyxel GS1920-8HP, I noticed that some areas on the Nebula Cloud Center weren’t active and, since I added the NSG50 to the network, we can now fully explore those areas. Before accessing the Nebula Cloud, you need to perform the hardware installation of the device which consists of plugging the power cord into the back of the switch and into a power socket and turning the device on using the ON/OFF switch; afterwards, take two Ethernet cables and use one to connect the gateway to your modem (the cable should be connected to the WAN port) and the second Ethernet cable should be connected to any of the four available LAN ports and to a computer – if you have a secondary Internet connection available, you need to use the SFP port.
After you have connected all the cables and powered on the NSG50, you need to open a web browser and go to the IP address of the gateway (it should be 192.168.1.1); at this point, you’ll be asked to enter the username and password and, by default they’re admin and 1234. Immediately after, you will have to change the admin password and, afterwards, you’ll gain access to the stand-alone user interface.
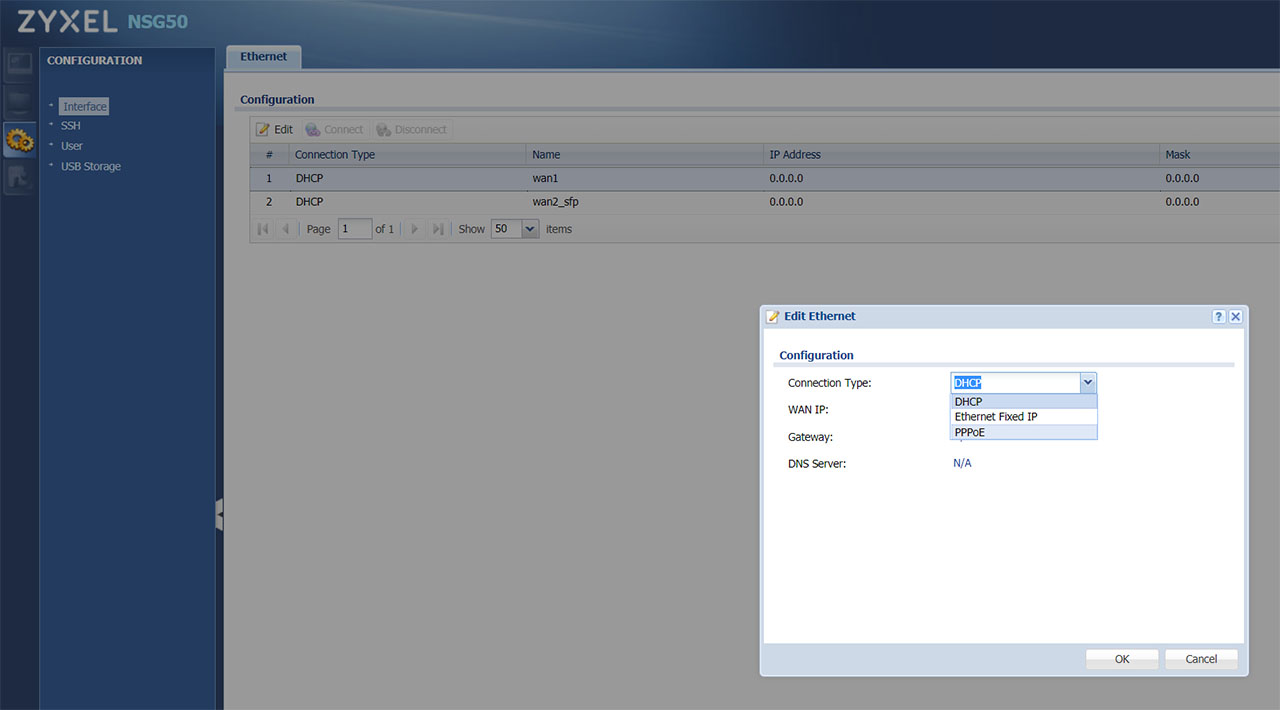
Since you may want to browse the web or register the Zyxel gateway to the Cloud, you’ll need access to the Internet, so you should go to Configuration, double-click the first WAN (it’s going to be DHCP > Wan1) and, at the configuration Type, select PPPoE; doing so, will summon additional areas for you to fill with the ISP username and password (you can enable the Nailed-Up feature if you run servers).
After you’ve followed these steps, you should have gained access to the Internet and, if you don’t care for the Nebula Cloud management software, you could continue exploring the stand-alone UI, but I must warn that some important features will be missing. The Dashboard will show you the Device Information (some general stats about the device), the System Status and the Extension Slot (USB) and the next main section that you can access from the left menu is the Monitor, where there’s the USB Storage area (Storage Information), while further down, there’s the Configuration section. Here, you can modify the Ethernet Configuration (configure the two available WAN ports – we have already visited this section to set up the Internet connection), the SSH (here, you can enable the Allow WAN to Device – insert the Client’s IP address), change the User’s password or Activate the USB storage service (will let you know when the disk is almost full).
Zyxel NSG50
Pros
- Remote management and monitoring using Nebula Cloud Center
- Security features: Antivirus, Firewall, IDP, VPN and more
- Good thermal performance
- Good integration with the other Zyxel devices (WAPS and Etherent Switches)
- Nebula app (iOS and Android OS)
Cons
- There are no storage related features on the NCC
- The NCC requires a bit of a learning curve

Mark is a graduate in Computer Science, having gathered valuable experience over the years working in IT as a programmer. Mark is also the main tech writer for MBReviews.com, covering not only his passion, the networking devices, but also other cool electronic gadgets that you may find useful for your every day life.